Bank-Grade Security
More Than Just an Image of a Digitized Signature
A signature captured with SIGNificant is much more than just an electronic image of a digitized signature. We record the handwritten signature of a person using all available parameters, such as acceleration, speed, and rhythm. These parameters are unique to every individual and cannot be reproduced by a forger. Thus the digitized signature is forensically identifiable.

Forensic Signature Verification
When someone claims “I didn’t sign that,” a forensic expert can perform a deep manual signature verification any time afterwards, using the SIGNificant PenAnalyst software just as they would with a signature on paper. In addition to this service, we also provide a signature verification that authenticates a signature against a pre-enrolled signature profile database in real time.
Learn More
Encryption of the Biometrical Signature Data
The biometrical signature data is encrypted asymmetrically using a public key directly while the signature is being recorded. Reading the signature for verification purposes is only possible by decrypting it with the corresponding private key, which can either be stored offline, e.g. at a notary, or when required online, for example in a High Security Module (HSM).

Binding the Signature to the Document
The signature is always securely bound to a unique document. The document's fingerprint is encrypted together with the signature data, making copy/paste attacks impossible.

Browse the Document on Signature Pads
We show the relevant part of the document as the background image on signature pads, to provide the signer a visual link between the signature and the document. On many signature pads we enable signers to browse through the whole document on the signature pad if they want to. Although the displays are typically not very large, this works quite well.
Trusted Timestamp and Geolocation
You can integrate nearly any time-stamp service you want to proof the exact signature date and increase legal compliance. In addition to this capability we embed the geolocation into the signature data if available.

Prove the Signer's Identity for Online Transactions
When capturing a forensically identifiable signature is not an option, you can choose different authentication methods for online transactions. Options range from email-only authentication, to leveraging trusted authentication models that you have already in place, to using a Facebook login, up to sending a text message with a one-time password to a signer’s mobile phone.
Get a Detailed Audit Trail
The audit trail is a powerful tool that can prove who signed a document and when they signed it. Our Audittrail keeps track of the following events and more:
- Emails and notifications sent
- Signer's consent to use e-signatures
- User authentication provided
- Pages viewed by each signer
- Signature creation
- Transaction completion
- Document downloads
- Cancellations

Tamper Evidence
Every time a signature is captured, a digital signature is also applied, which turns the document into a sealed PDF, making undetectable changes of the document content impossible. As a result, documents are tamper-evident not just at the end of the signing process, but from the moment the transaction is started.
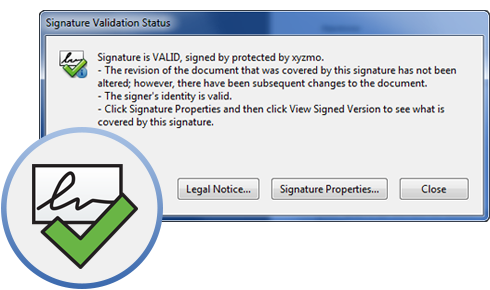
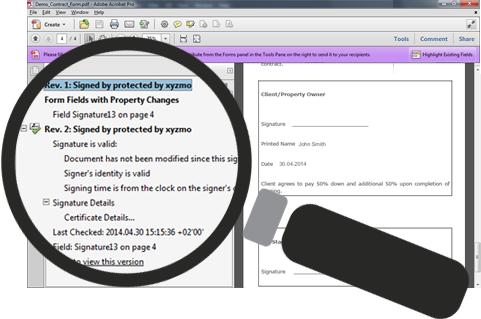
True Digital Signatures
Our signatures are true digital signatures based on documented technical standards that are not proprietary to Namirial. SIGNificant-signed documents can be easily verified using free PDF reader software. There’s no need to go to our website for that.
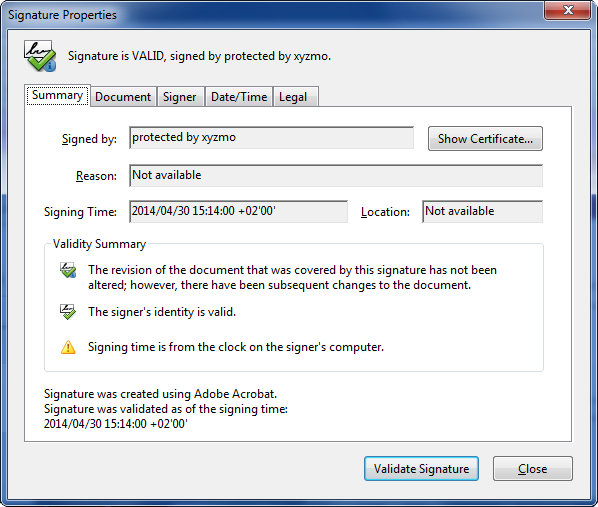
View Document History
By using true digital signatures we record a history of what each document looked like at the time it was signed. The history is embedded into the document. You can take a look at the embedded signature history within compliant PDF viewers, even if you're not connected to the internet. In this way, you can see exactly how the document looked when each signer signed it.